Strong password habits are essential to protecting personal and professional data from cyber threats. Weak passwords are one of the biggest security risks, making it easier for hackers to gain unauthorized access to accounts. In an increasingly digital world, following the best practices for password security can reduce the risk of data breaches and identity theft.
Best Password Protection Practices
- Use Unique Passwords for Each Account Reusing passwords across multiple accounts increases the risk of a security breach. If one password is compromised, hackers can access all accounts that share the same credentials.
- Create Complex Passwords A strong password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessed words like “password” or “123456”.
- Enable Multi-Factor Authentication (MFA) MFA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone or an authentication app.
- Use a Password Manager Password managers help generate and store complex passwords securely. This reduces the need to remember multiple passwords while keeping them protected. Apple’s iCloud Keychain is a perfect example.
- Avoid Sharing Passwords Sharing passwords, even with trusted individuals, increases the risk of unauthorized access. If you need to send an email, Office365 has the option to make emails encrypted with the following steps:
- Creating a new email
- Going to ‘Options:
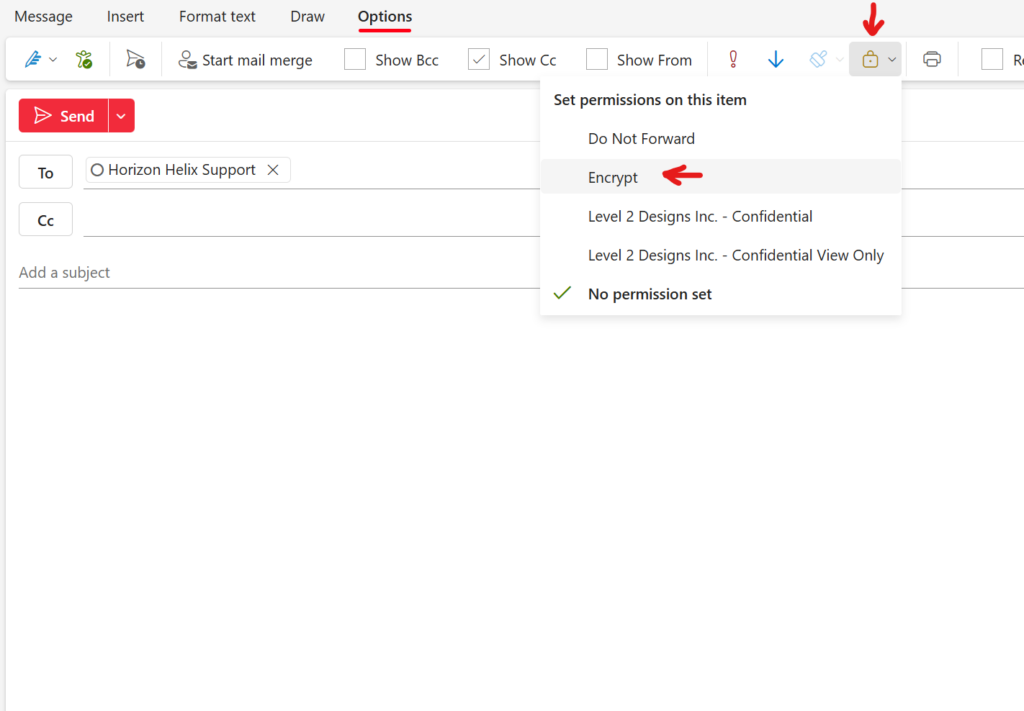
- Finding the lock button in the upper right corner of the task bar and selecting ‘Encrypt’:
*A second option is to simply type “confidential” in the subject line to encrypt the email, and this will still show the word “confidential” in the subject line as seen above. This can be done at any point in the subject line.
- Change Passwords Periodically Regularly updating passwords helps minimize the risk of long-term exposure in case of a security breach. Change passwords immediately if you suspect any unauthorized access.
- Be Cautious of Phishing Attacks Cybercriminals use phishing emails and fake websites to trick users into revealing their passwords. Always verify the legitimacy of emails and websites before entering credentials. For example, a fraudulent website may replace easily mistakable letters like uppercase “i” for lowercase “L”. This could look as convincing as PayPaI(.)com If you ever feel that the URL may be compromised, you can always type the URL you know to be correct manually.
By adopting these password protection habits, you can strengthen your online security and reduce the risk of cyber threats. Taking a proactive approach to password management is a simple yet effective way to safeguard your personal and professional information. Taking an extra minute to verify if something is legitimate may save hours of hassle.



